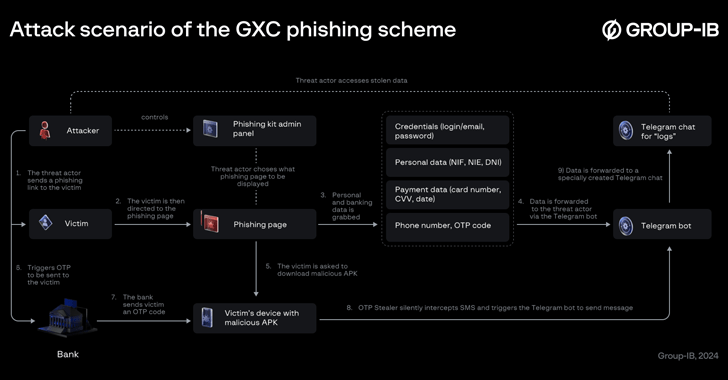
This AI-Powered Cybercrime Service Bundles Phishing Kits with Malicious Android Apps A Spanish-speaking cybercrime group named GXC Team has been observed bundling phishing kits with malicious Android applications, taking malware-as-a-service …
Category:
Cyber Security
Offensive AI: The Sine Qua Non of Cybersecurity “Peace is the virtue of civilization. War is its crime. Yet it is often in the furnace of war that the sharpest …
- Cyber SecurityTechnology
Crypto exchange Gemini discloses third-party data breach
by Wire Techby Wire TechCryptocurrency exchange Gemini is warning it suffered a data breach incident caused by a cyberattack at its Automated Clearing House (ACH) service provider, whose name was not disclosed. The American …
- Cyber SecurityTechnology
FBCS data breach impact now reaches 4.2 million people
by Wire Techby Wire TechDebt collection agency Financial Business and Consumer Solutions (FBCS) has again increased the number of people impacted by a February data breach, now saying it affects 4.2 million people in …
- Cyber Security
U.S. DoJ Indicts North Korean Hacker for Ransomware Attacks on Hospitals
by Wire Techby Wire TechU.S. DoJ Indicts North Korean Hacker for Ransomware Attacks on Hospitals The U.S. Department of Justice (DoJ) on Thursday unsealed an indictment against a North Korean military intelligence operative for …
- Cyber Security
North Korean Hackers Shift from Cyber Espionage to Ransomware Attacks
by Wire Techby Wire TechNorth Korean Hackers Shift from Cyber Espionage to Ransomware Attacks A North Korea-linked threat actor known for its cyber espionage operations has gradually expanded into financially-motivated attacks that involve the …
- Cyber SecurityTechnology
PKfail Secure Boot bypass lets attackers install UEFI malware
by Wire Techby Wire TechHundreds of UEFI products from 10 vendors are susceptible to compromise due to a critical firmware supply-chain issue known as PKfail, which allows attackers to bypass Secure Boot and install …
- Cyber SecurityTechnology
Critical ServiceNow RCE flaws actively exploited to steal credentials
by Wire Techby Wire TechThreat actors are chaining together ServiceNow flaws using publicly available exploits to breach government agencies and private firms in data theft attacks. This malicious activity was reported by Resecurity, which, …
- Cyber Security
6 Types of Applications Security Testing You Must Know About
by Wire Techby Wire Tech6 Types of Applications Security Testing You Must Know About Application security testing is a critical component of modern software development, ensuring that applications are robust and resilient against malicious …
Newer Posts