Across small-to-medium enterprises (SMEs) and managed service providers (MSPs), the top priority for cybersecurity leaders is to keep IT environments up and running. To guard against cyber threats and prevent data breaches, it’s vital to understand the current cybersecurity vendor landscape and continually assess the effectiveness of available solutions.
Luckily, the 2024 MITRE ATT&CK Evaluation — the most widely trusted resource to track which solutions are effective — is now available. This practical guide distills key takeaways and advice to interpret the results.
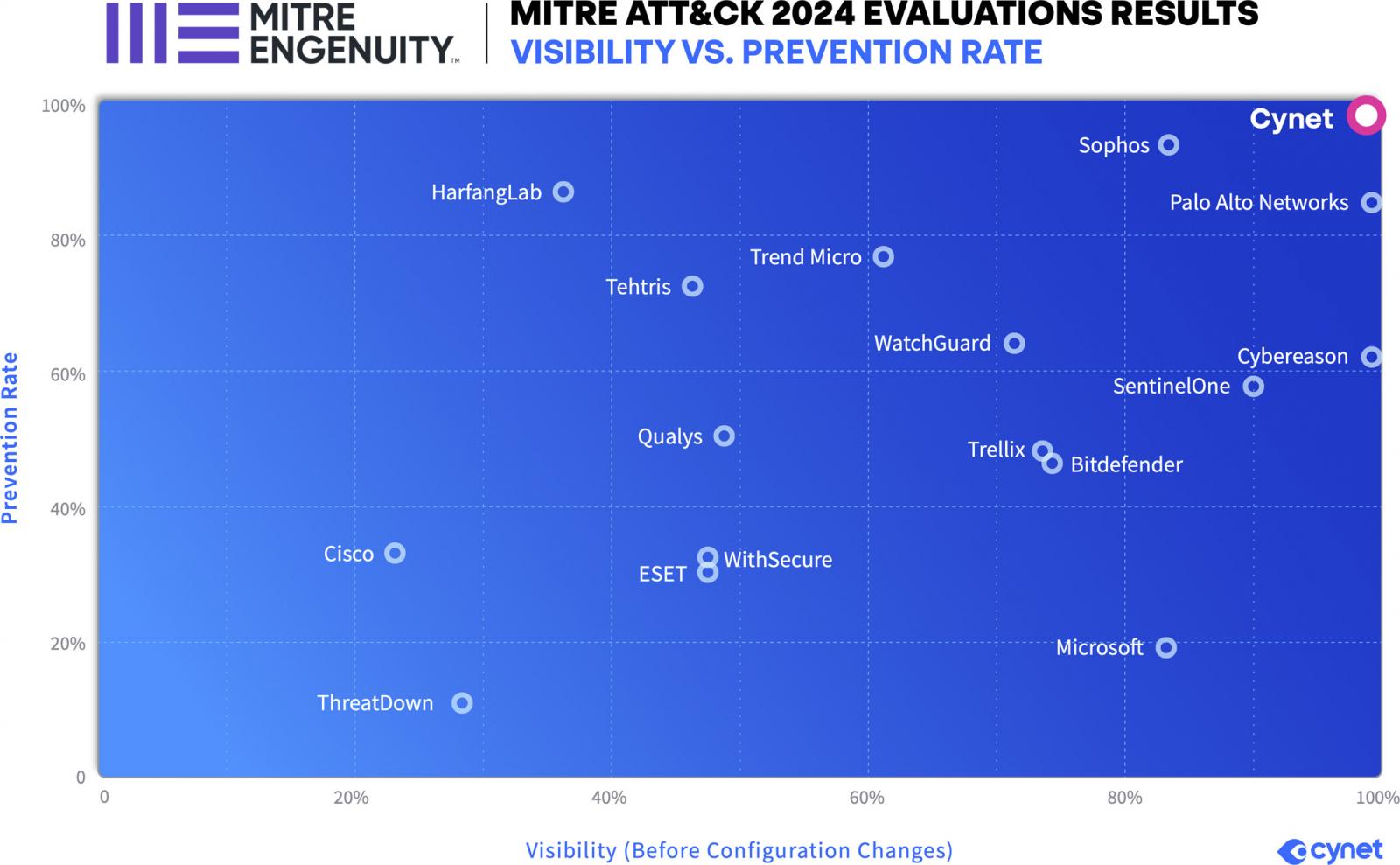
Cynet was the only vendor to achieve 100% Visibility and 100% Protection in the 2024 Evaluation.
That means the All-in-One Cybersecurity Platform detected 100% of the threats tested in the Detection Phase and blocked 100% of the attacks simulated in the Protection Phase of the Evaluation. Moreover, Cynet achieved the 100% detection with no false positives.
“These 2024 MITRE ATT&CK Evaluation results reflect our entire team’s commitment to secure success for Cynet partners, customers, and end users,” says Cynet Founder & CEO Eyal Gruner. “Achieving 100% Detection Visibility and 100% Protection is a motivating milestone that affirms the compelling advantages Cynet’s All-in-One Cybersecurity Platform is enabling for organizations around the world.”
This 2024 performance is notable after Cynet made history in the 2023 MITRE ATT&CK Evaluation. It was the first time ever a vendor delivered 100% Visibility and 100% Analytic Coverage with no configuration changes. However, it is important to note that MITRE does not rank vendors or declare “winners.” Cybersecurity leaders must interpret the data to determine which solution best fits their team’s unique needs.
What is the MITRE ATT&CK Evaluation?
MITRE is a nonprofit foundation that supports private sector companies “solving problems for a safer world.” Their annual ATT&CK Evaluation is regarded as the fairest and most unbiased technical test of competing security vendor solutions.
- MITRE uses simulated attacks in a controlled lab environment to evaluate how vendor solutions behave against a set of threats introduced in the exact same manner.
- Vendor solutions are tested consistently, without external, extraneous factors influencing the results as is the case in a real-world deployment.
This approach helps evaluate how effectively a solution can detect an abundance of discrete steps that might be used by an adversary to carry out an attack. Because MITRE uses the techniques of real threat groups, each technique presented represents what is likely to happen in a real-world scenario.
The Evaluation allows vendors to demonstrate whether their solution detects the threats presented as well as the information provided with each detection.
KEY RESULTS
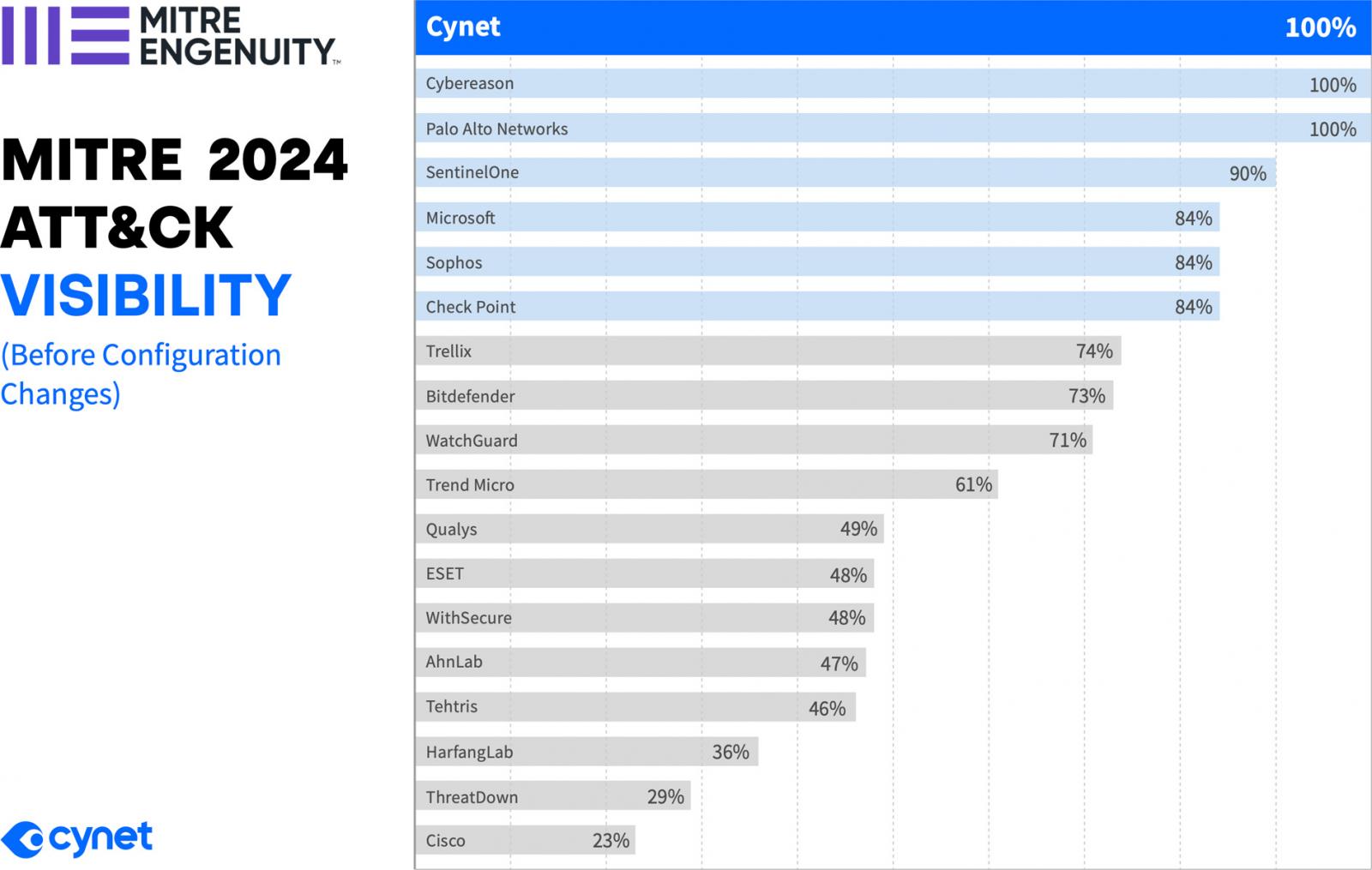
Cynet delivered 100% Detection Visibility, perfectly detecting every attack action using no configuration changes and no delays.
The ability to detect threats is the fundamental measure of an endpoint protection solution. Detecting attack steps across the MITRE ATT&CK sequence is critical for protecting the organization. Missing any step can allow the attack to expand and ultimately lead to a breach or other catastrophic outcomes.
This year, the attack sequence was executed over 16 steps, which were broken out into 80 malicious sub-steps. During Cynet’s testing, 3 of the sub-steps were not executed due to technical reasons and are considered N/A (not counted) which resulted in 77 total sub-step executed. Cynet detected every single one of the 77 sub-steps. Cynet had ZERO misses in this year’s MITRE testing and detected 100% of attacks over Windows and MacOS devices as well as Linux servers.
All 77 detections were performed without the need for configuration changes. Leaders reviewing vendor outcomes can see which vendors could accomplish detections only after they were allowed to make configuration changes.
Cynet delivered 100% Protection, blocking every attack sequence attempted.
Roughly half of the participating security vendors were unable to test all 10 attack steps planned for the Protection tests due to technical issues. MITRE was able to execute all 10 attack steps for Cynet. Cynet blocked every one of the 10 attacks steps – allowing no malicious activity to execute.
The following chart shows each participant’s Protection rate along with the number of steps blocked and number of steps executed (steps blocked/steps executed).
Cynet delivered 100% Prevention, blocking every attack in the first step attempted.
Protection measures whether any sub-step in a Protection step was blocked. For example, if a step consisted of 5 sub-steps, a vendor could miss the first four, block the fifth and consider the entire step blocked. Cynet defines Prevention as how quickly (early) in each of the 10 attack steps the threat was prevented.
Prevention measures the percentage of sub-steps that were blocked from executing. Ideally a vendor would block the first sub-step in every step tested so that every subsequent sub-step in the step was considered to be blocked. Using this measure, Cynet is the only vendor to achieve 100% Prevention – blocking every one of the 21 Protection sub-steps from executing.
Cynet is the leader in Overall Threat Visibility and Protection
The chart below compares each vendors overall visibility with prevention rate. Prevention rate is used as it’s a more rigorous measure of the solutions ability to block malicious attacks.
Conclusion
Partnering with the right cybersecurity vendor is one of the first and most effective steps you can take to enable the best protection possible for your organization or your clients.
The 2024 MITRE ATT&CK Evaluation results substantiate why Cynet’s All-in-One Cybersecurity Platform is an increasingly popular solution for fast-growing SMEs and MSPs.
By demonstrating that highly effective protection can be truly intuitive and affordable, Cynet sets an example competing vendors must now strive to emulate.
Sign up to see Cynet in action today.
Sponsored and written by Cynet.
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




