Threat actors are using public exploits for a critical authentication bypass flaw in ProjectSend to upload webshells and gain remote access to servers.
The flaw, tracked as CVE-2024-11680, is a critical authentication bug impacting ProjectSend versions before r1720, allowing attackers to send specially crafted HTTP requests to 'options.php' to change the application's configuration.
Successful exploitation allows the creation of rogue accounts, planting webshells, and embedding malicious JavaScript code.
Though the flaw was fixed on May 16, 2023, it was not assigned a CVE until yesterday, leaving users unaware of its severity and the urgency of applying the security update.
According to VulnCheck, which has detected active exploitation, the patching pace has been abysmal so far, with 99% of ProjectSend instances still running a vulnerable version.
Thousands of instances exposed
ProjectSend is an open-source file-sharing web application designed to facilitate secure, private file transfers between a server administrator and clients.
It is a moderately popular application used by organizations that prefer self-hosted solutions over third-party services like Google Drive and Dropbox.
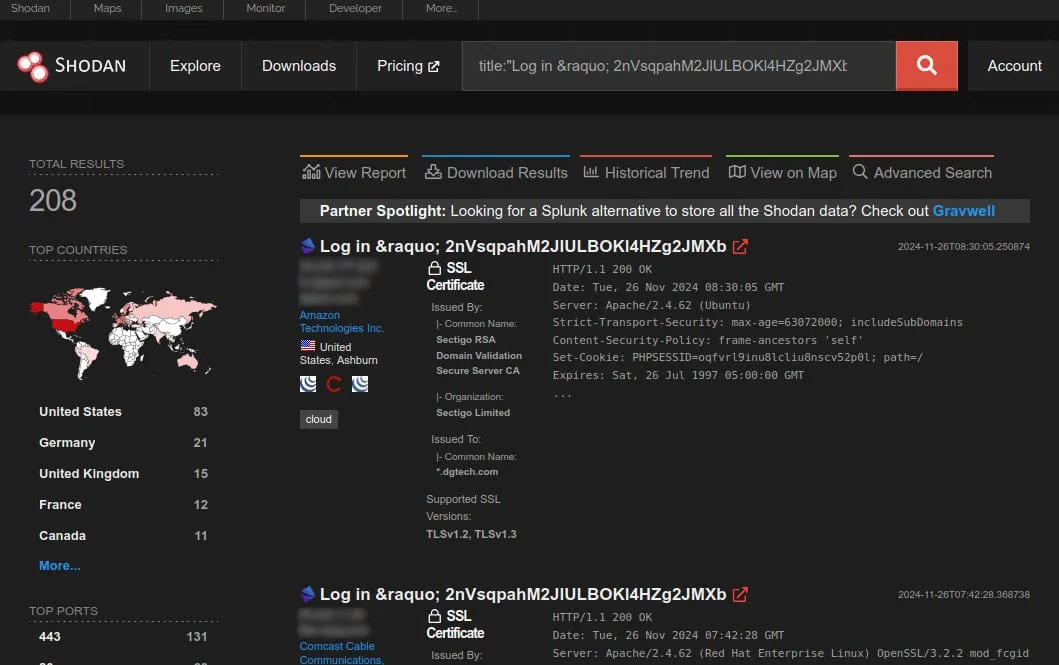
Censys reports that there are roughly 4,000 public-facing ProjectSend instances online, most of which are vulnerable, says VulnCheck.
Specifically, the researchers report that, based on Shodan data, 55% of the exposed instances run r1605, released in October 2022, 44% use an unnamed release from April 2023, and only 1% is on r1750, the patched version.
VulnCheck reports seeing active exploitation of CVE-2024-11680 that extends beyond just testing, including altering system settings to enable user registration, gaining unauthorized access, and deploying webshells to maintain control over compromised servers.
Source: VulnCheck
This activity increased since September 2024, when Metasploit and Nuclei released public exploits for CVE-2024-11680.
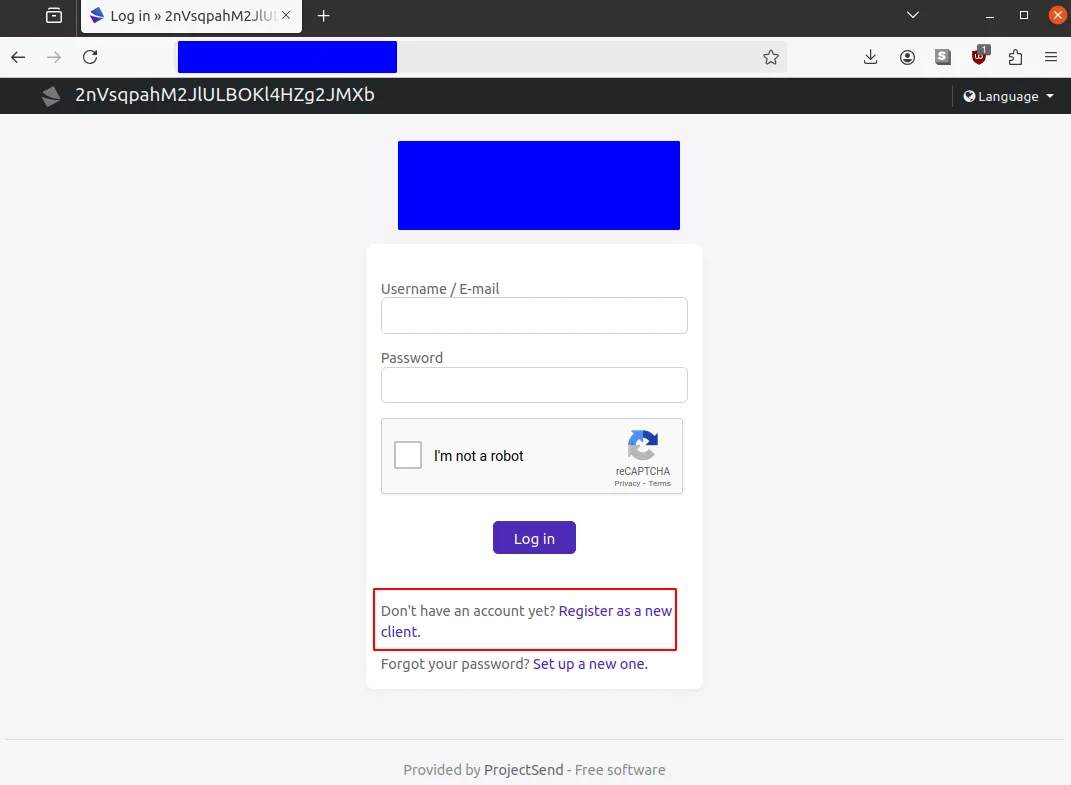
"VulnCheck noticed that public-facing ProjectSend servers had started to change their landing page titles to long, random-ish strings," reads the report.
"These long and random-ish names are in line with how both Nuclei and Metasploit implement their vulnerability testing logic."
"Both exploit tools modify the victim's configuration file to alter the sitename (and therefore HTTP title) with a random value."
GreyNoise lists 121 IPs linked to this activity, suggesting widespread attempts rather than an isolated source.
Source: VulnCheck
VulnCheck warns that the webshells are stored in the 'upload/files' directory, with names generated from a POSIX timestamp, the username's SHA1 hash, and the original file name/extension.
Direct access to these files through the web server indicates active exploitation.
The researchers warn that upgrading to ProjectSend version r1750 as soon as possible is critical as attacks are likely already widespread.
Related Articles:
Hackers target critical zero-day vulnerability in PTZ cameras
CISA tags Progress Kemp LoadMaster flaw as exploited in attacks
Oracle warns of Agile PLM file disclosure flaw exploited in attacks
Security plugin flaw in millions of WordPress sites gives admin access
Critical bug in EoL D-Link NAS devices now exploited in attacks
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




