Welcome to our Information Security series. Over the long history of the humankind, information has been always a vital asset. Pieces of information together make knowledge, and accumulated information make experience.
A small piece of information (that may look trivial to some or most people) may ignite a war. And another could decide the result of a long war. In economy, a tiny piece of information may cause the stock exchange market to suffer huge losses, and may be the opposite.
Inaccurate information on the board of directors table will certainly mislead the top management of the corporation to take wrong decision, that may result at the end in a financial loss and / or bad reputation, and even worse: the corporation may get out of market forever.
Absence of critical information (or being unable to prove it on the right time) may cause a lawyer to lose a case for a client (individual or organization) resulting in serious consequences for both: the client and the lawyer.
Wow!! To this great extent information is crucial ?!
And even more than you could imagine.
For the above reasons and many others, securing information has become no longer a luxury.
Nowadays, with the continuously increasing dependence on information and computer systems, the need for Information security becomes of utmost importance.
Securing Information against what?!
A good question that we are going to reply. soon!!
What Information Security aims to do?
Information security aims to protect information against all possible sorts of threats that may put information – and its owner(s) – in danger. All these threats can be grouped together and be summarized under the following three main threat categories:
- Threat that information be disclosed to others who should not know about it.
- Threat that information be altered, changed, or manipulated in someway by person(s) who should not do.
- Threat that information be blocked, hidden, or denied access to people who should have access to it, on need.
So, Information Security aims to protect (secure) information against the above three main threat types.
Have I replied your question now?
Yes, thanks, but how such protection will be achieved?
Just wait till we finish replying the question: what information security aims to do?
CIA Triangle
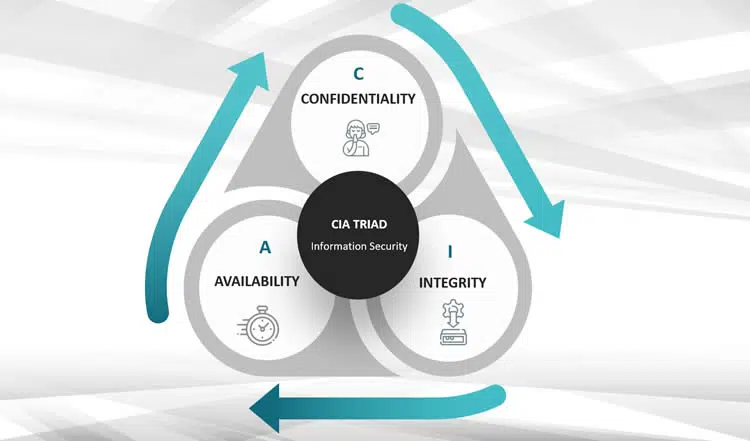
The CIA Triangle (or Triad) summarizes the main objectives that Information Security aims to achieve.
- C stands for Confidentiality.
- I stands for Integrity.
- A stands for Availability.
Let’s discuss them one by one in some details.
Confidentiality
Confidentiality aims to assure secrecy of data. In simple words: implementing and protecting Confidentiality are supposed to:
- Prevent un-authorized access to data.
- Allow only authorized people to read or access data.
Who Cares most about Confidentiality?
Data Confidentiality will be crucial in several situations:
- In Military Affairs.
- In Intelligence Agencies.
- In Bureaus of Investigations.
- In companies, when preparing a marketing campaign for a new product.
- For a lawyer working on a case, where data, documents, and/or evidences must be kept confidential.
- Privacy of Medical information for individuals in some countries (For more info try to read about “HIPAA”).
How to Protect Confidentiality?
Protecting Confidentiality can be achieved using many methods (security controls). Examples for possible methods are:
- Encrypting data.
- Controlling Access to data (via several techniques or methods).
- Information Security Awareness campaigns for staff.
- Strong Authentication methods.
1. Integrity
Data Integrity can be defined as ensuring data accuracy and correctness. Protecting data integrity means to prevent any possible form of unauthorized tampering, manipulation, or alteration of data.
To maintain data integrity, we must assure that all of the following three conditions are fulfilled together:
- To prevent un-authorized persons from altering data.
- To prevent authorized persons from making malicious alteration of data.
- To protect data against any accidental, un-intended mistake done by authorized persons.
Who should Care most about Data Integrity?
In addition to the above ones mentioned under “Who Cares most about Confidentiality?” , the following also must see data integrity as of utmost importance:
- Financial authorities.
- Banks.
- Stock Exchange.
- Legal Authorities.
Try to imagine that you have received an SMS from the bank you deal with telling that your account balance has suddenly decreased by 10 thousand US dollars.
Imagined and got scared?! Okay! You now understand why data integrity is very crucial.
How to Protect Data Integrity?
The following security controls can help protect data integrity:
- Strong Authentication.
- Strict Access Control.
- Data Encryption.
- Using Hashes (checksums).
- Information Security Awareness Training for users.
- Data Validation.
- Logs and Audit Trails.
What is a Security Control?
A Security Control is any method, mechanism, procedure, or technique that is used or implemented to detect, mitigate, avoid, reduce, minimize, or prevent possible risks on the data or assets of a corporation.
Possible alternatives to the expression “Security Controls” are Countermeasures and Safeguards.
2. Availability
Maintaining Data Availability means that data should be accessible in a timely manner to authorized people on need.
The common threats to data or availability includes but are not limited to:
- Denial of service (DoS) attacks.
- Hardware Failures.
- Software problems.
- Accidental deletion of data.
- Power Blackouts.
- Communication Issues.
- Administrator Mistakes.
Who should Care most about Data Availability?
In addition to all parties that were mentioned while talking about Confidentiality and Integrity, the following also should care about protecting data availability:
- Call Centers.
- E-Commerce Websites.
- Hotels’ E-booking websites.
How to Ensure Data Availability?
To maintain Data Availability, the following safeguards and precautions would help:
- Implementing High-availability (Active-Active, or Active-Passive).
- Using Access Control.
- Using Firewalls and Intrusion Prevention Systems to protect against DoS attacks.
- Maintaining Backups for operating systems and data.
- Testing Backups periodically to make sure they are reliable and could be restored successfully.
- Using Redundant Storage, Switches, Routers, and Firewalls.
- Having a Disaster Recovery (DR) site, that you can switch systems to in case the main production site becomes unavailable.
- Using Multiple Power Sources.
- Using Un-interruptible Power Supply (UPS).
- Using Electric Generator.
- Periodic BCP (Business Continuity Plan) tests.
- Avoiding Single Points of Failure when designing and implementing systems.
An available data will be worthless if it is not correct and accurate. So, Availability depends mainly on Integrity.
The Security Wheel
Unfortunately, security is not a one-shot project!! Security is continuous cycle that never ends.
Sounds frustrating?! But that is the truth!!
Why Security is considered as “Continuous” process? The answer is that threats to an organization’s data and assets never stop. Hackers never take rest!!
Every moment there is a hacker somewhere on the planet working on an open port trying to invade it, on a webpage trying to detect any field with insufficient input validation check to exploit and make SQL injections, Buffer overflow, or cross site scripting.
There are also password crackers who try to guess passwords using techniques like brute-force and dictionary attacks, in order to gain access to systems, or websites to steal data, alter data, or take it down completely (DoS).
Even when you install a security patch that a vendor recommends to fix a vulnerability!! Several days, weeks, or months later, hackers may detect a new vulnerability in the security patch code itself!! Modern hardware’s with very powerful processors caused an encryption algorithm that was considered (3 or 5 years ago) as impossible (or requires years) to break to be breakable now.
Hacking and cracking attempts never stop. So, security efforts should never stop!!

The on-going security process starts by identifying the specific countermeasures (security controls) required to secure the organization’s assets. After fully identifying these requirements, we come to the first step:
1. Secure:
This step can be also called “Implement”. The organization implements the necessary security controls. This can include but not limited to: Security patching, implementing firewalls, Intrusion Prevention Systems, Encryption, Strict Access Controls, Strong Password Policy, and Security Awareness courses for users.
At this point, the organization assets seems to be secure. Now Step 2 comes.
2. Monitor
Now, the organization should monitor the effectiveness of the implemented safeguards, and whether they were able to eliminate, mitigate, minimize, reduce, or at least detect security attacks and / or breaches or not.
This process includes reviewing various system logs: firewall logs, IPS logs, server logs, etc.
3. Test
To actively test how sufficient the implemented safeguards are, and how they would respond when put under real attack scenarios.
This step is done by contracting with a company specialized in “Penetration Testing”. The company will try to its best to break through your defenses in order to gain access to the assets / systems/ data (of course with no real harm on either of them).
After the test is over, the company will provide you with a detailed report of what they have done, the vulnerable (weak) points they exploited to penetrate your defenses, and finally the most important part that is: what are their recommendations to “improve” your security posture.
4. Improve
Based on the findings and results collected from the Monitor and Test steps, the organization will re-evaluate the entire security posture, and decide what improvements should be done to increase the effectiveness of the implemented security controls.
Improvements could be actions like: modifying firewall rules (access list), tuning Intrusion Prevention System IPS, using stronger encryption algorithms, implementing physical security, using more strict access control mechanisms, and investing more time and money in raising the security awareness for users.
This 4-steps process should be continuously repeated to guarantee the continuous enhancement of the organization’s security.
Subjects Vs Objects
There are two main terms that we need to understand before talking about Access Control: Subjects and Objects.
A Subject is the active entity that initiates or attempts access to a resource.
An Object is the passive entity, which is the data or resource that the subject is attempting to access.
A Subject could be a user, process (computer program), or a client computer. While an object could be a file, directory, network port, server, or printer.
Together, Subjects and Objects are the main components of the Access Control Model.
In the next article, we are going to discuss the AAA (Triple A) Concept.




