The Play ransomware gang has claimed responsibility for a cyberattack that impacted the business operations of the U.S. doughnut chain Krispy Kreme in November.
Krispy Kreme disclosed the incident and subsequent disruptions to its online ordering system in an SEC filing submitted on December 11. The company detected unauthorized activity on some of its information technology systems on November 29.
After the attack, Krispy Kreme also took measures to contain and remediate the breach and hired external cybersecurity experts to investigate the attack's impact and scope.
"We're experiencing certain operational disruptions due to a cybersecurity incident, including with online ordering in parts of the United States," Krispy Kreme said in a message on its official website.
"We know this is an inconvenience and are working diligently to resolve the issue. [..] We'll have our online ordering up as soon as we can. Our fresh doughnuts are available in our shops as always!"
Krispy Kreme's Q3 2024 financial results show that digital orders represent 15.5% of the company’s sales, contributing to its 3.5% organic revenue growth in Q3 2024.
The American multinational coffeehouse chain and doughnut company operates 1,521 shops and 15,800 points of access, four "Doughnut Factories" in the United States, and 37 others internationally. As of December 2023, it employed 22,800 people in 40 countries. Krispy Kreme also partners with McDonald's to have its products sold in thousands of additional McDonald’s locations worldwide.
While the company has yet to share additional details about the attack and, when approached by BleepingComputer for comment, shared a statement similar to the one filed with the SEC, the Play ransomware gang has now claimed the November breach and says they also allegedly stole data from the company's network.
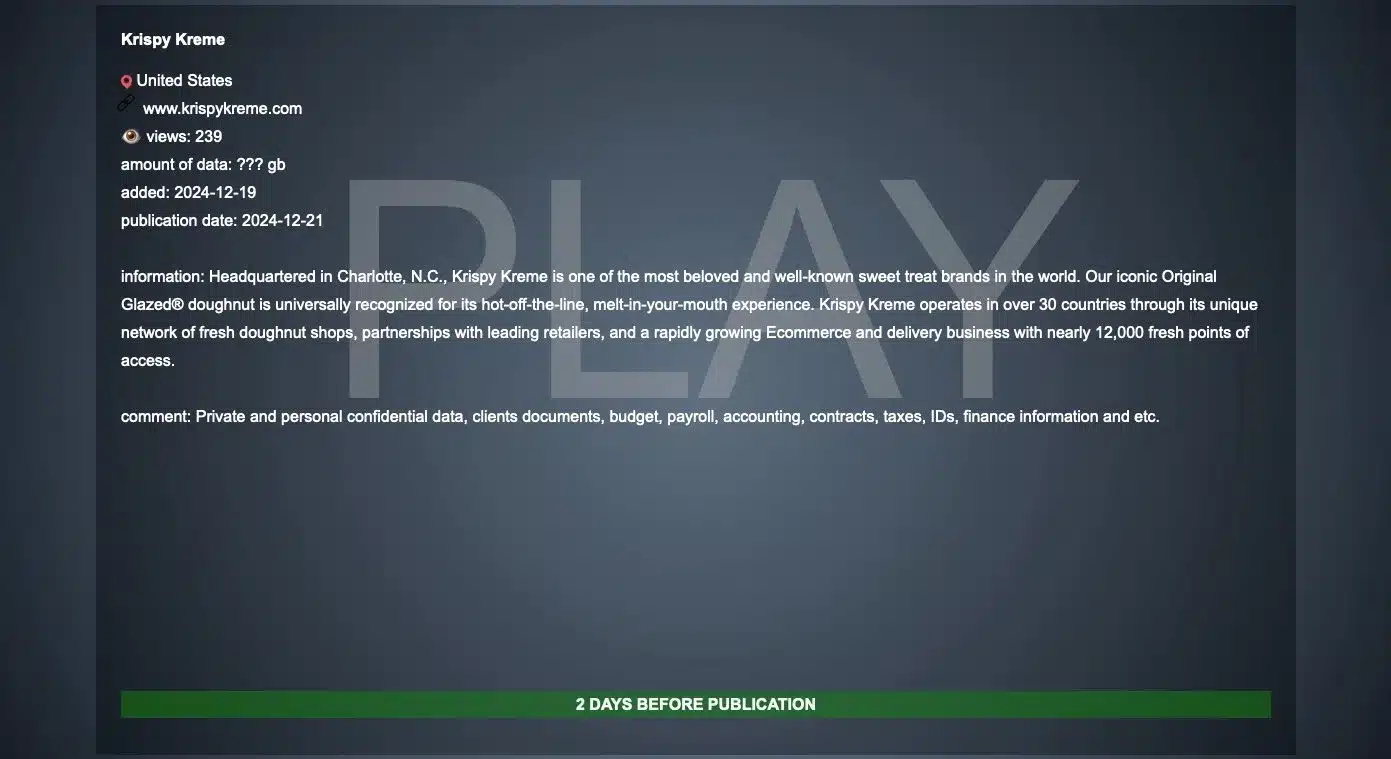
Play ransomware claims, without proof, that they collected and stole files containing "private and personal confidential data, client documents, budget, payroll, accounting, contracts, taxes, IDs, finance information," and more. The attackers now say they'll publish the data this Saturday, November 21.
The Play ransomware operation surfaced over two years ago, in June 2022, with initial victims seeking help through BleepingComputer's forums. Play operators steal sensitive data from breached systems to use in double-extortion schemes, pressuring victims into paying ransoms to avoid having the stolen data leaked online.
Previous notable Play ransomware victims include car retailer giant Arnold Clark, cloud computing company Rackspace, the City of Oakland in California, Dallas County, the Belgian city of Antwerp, and, most recently, American semiconductor supplier Microchip Technology.
The FBI issued a joint advisory with CISA and the Australian Cyber Security Centre (ACSC) last December, warning that the Play ransomware operation had breached the networks of around 300 organizations worldwide as of October 2023.
Related Articles:
Clop ransomware claims responsibility for Cleo data theft attacks
Blue Yonder SaaS giant breached by Termite ransomware gang
CISA says BianLian ransomware now focuses only on data theft
BT unit took servers offline after Black Basta ransomware breach
City of Columbus: Data of 500,000 stolen in July ransomware attack
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




