An active campaign from a threat actor potentially linked to Russia is targeting Microsoft 365 accounts of individuals at organizations of interest using device code phishing.
The targets are in the government, NGO, IT services and technology, defense, telecommunications, health, and energy/oil and gas sectors in Europe, North America, Africa, and the Middle East.
Microsoft Threat Intelligence Center tracks the threat actors behind the device code phishing campaign as 'Storm-237', Based on interests, victimology, and tradecraft, the researchers have medium confidence that the activity is associated with a nation-state operation that aligns with Russia's interests.
Device code phishing attacks
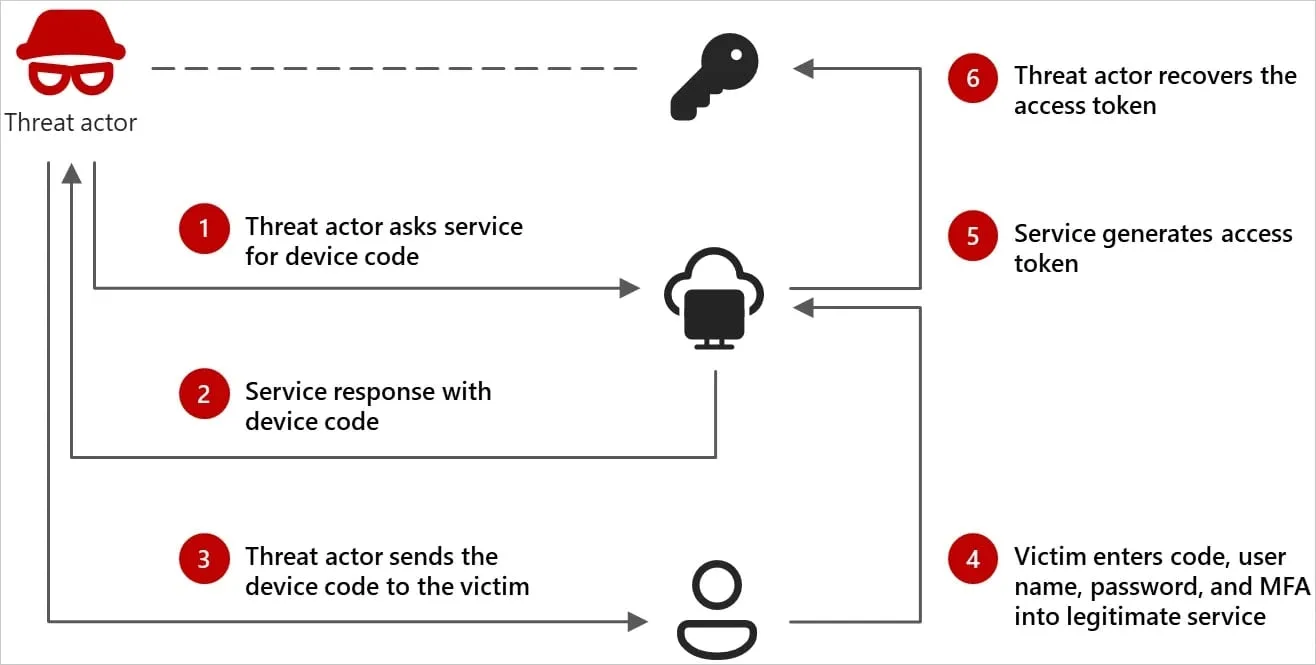
Input constrained devices – those that lack keyboard or browser support, like smart TVs and some IoTs, rely on a code authentication flow to allow allowing users to sign into an application by typing an authorization code on a separate device like a smartphone or computer.
Microsoft researchers discovered that since last August, Storm-2372 abuses this authentication flow by tricking users into entering attacker-generated device codes on legitimate sign-in pages.
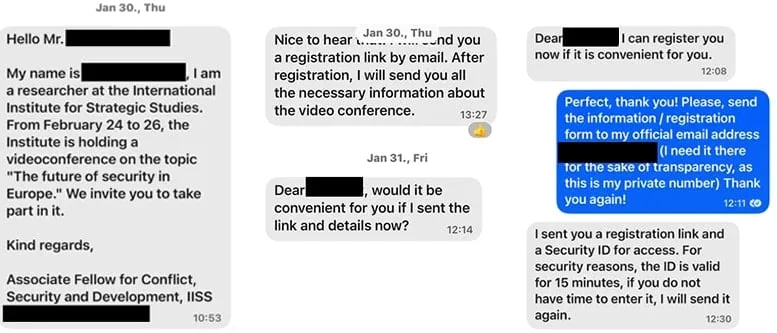
The operatives initiate the attack after first establishing a connection with the target by "falsely posing as a prominent person relevant to the target" over messaging platforms like WhatsApp, Signal, and Microsoft Teams.
Source: Microsoft
The threat actor gradually establishes a rapport before sending a fake online meeting invitation via email or message.
According to the researchers, victim receives a Teams meeting invite that includes a device code generated by the attacker.
"The invitations lure the user into completing a device code authentication request emulating the experience of the messaging service, which provides Storm-2372 initial access to victim accounts and enables Graph API data collection activities, such as email harvesting," Microsoft says.
This gives the hackers access to the victim's Microsoft services (email, cloud storage) without needing a password for as long as the stolen tokens remain valid.
Source: Microsoft
However, Microsoft says that the attacker is now using the specific client ID for Microsoft Authentication Broker in the device code sign-in flow, which allows them to generate new tokens.
This opens new attack and persistence possiblities as the threat actor can use the client ID to register devices to Entra ID, Microsoft's cloud-based identity and access management solution.
"With the same refresh token and the new device identity, Storm-2372 is able to obtain a Primary Refresh Token (PRT) and access an organization’s resources. We have observed Storm-2372 using the connected device to collect emails" – Microsoft
Defending against Storm-2372
To counter device code phishing attacks used by Storm-2372, Microsoft proposes blocking device code flow where possible and enforcing Conditional Access policies in Microsoft Entra ID to limit its use to trusted devices or networks.
If device code phishing is suspected, immediately revoke the user's refresh tokens using 'revokeSignInSessions' and set a Conditional Access Policy to force re-authentication for affected users.
Finally, use Microsoft Entra ID's sign-in logs to monitor for, and quickly identify high volumes of authentication attempts in a short period, device code logins from unrecognized IPs, and unexpected prompts for device code authentication sent to multiple users.
Related Articles:
Hackers spoof Microsoft ADFS login pages to steal credentials
Microsoft fixes bug causing Windows Server 2025 boot errors
Windows 10 KB5051974 update force installs new Microsoft Outlook app
Microsoft February 2025 Patch Tuesday fixes 4 zero-days, 55 flaws
Windows 11 KB5051987 & KB5051989 cumulative updates released
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




