A previously undocumented ransomware payload named NailaoLocker has been spotted in attacks targeting European healthcare organizations between June and October 2024.
The attacks exploited CVE-2024-24919, a Check Point Security Gateway vulnerability, to gain access to targeted networks and deploy the ShadowPad and PlugX malware, two families tightly associated with Chinese state-sponsored threat groups.
Orange Cyberdefense CERT links the attacks to Chinese cyber-espionage tactics, though there's not enough evidence to attribute them to specific groups.
NailaoLocker details
Orange's researchers report that NailaoLocker is a relatively unsophisticated ransomware strain compared to the most prominent families in the space.
The reason why Orange sees NailaoLocker as a rather basic ransomware is that, it does not terminate security processes or running services, it lacks anti-debugging and sandbox evasion mechanisms, and does not scan network shares.
"Written in C++, NailaoLocker is relatively unsophisticated and poorly designed, seemingly not intended to guarantee full encryption," mentions Orange.
The malware is deployed on target systems via DLL sideloading (sensapi.dll) involving a legitimate and signed executable (usysdiag.exe).
The malware loader (NailaoLoader) verifies the environment by performing memory address checks and then decrypts the main payload (usysdiag.exe.dat) and loads it into memory.
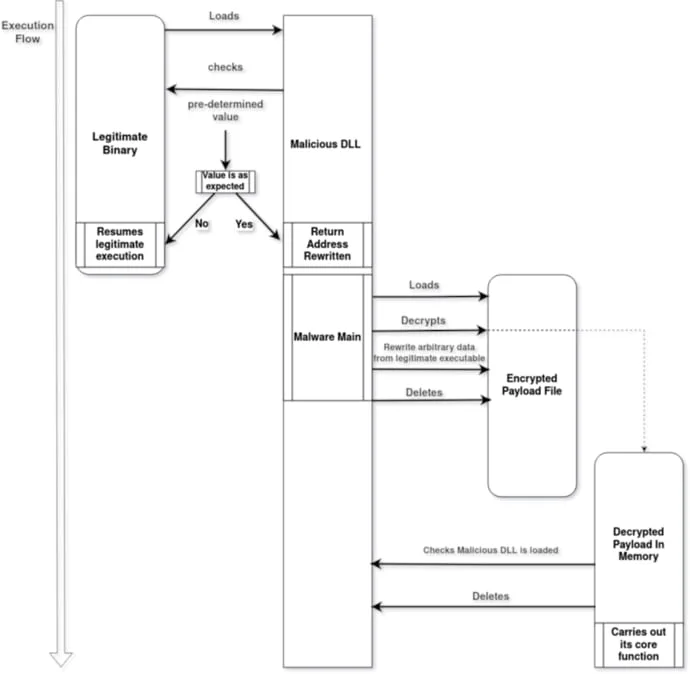
Source: Orange CERT
Next, the NailaoLocker activates and begins encrypting files using an AES-256-CTR scheme, appending the ".locked" extension to encrypted files.
After the encryption is done, the ransomware drops an HTML ransom note with the very unusually long filename of "unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please_view_this_file_unlock_please.html."
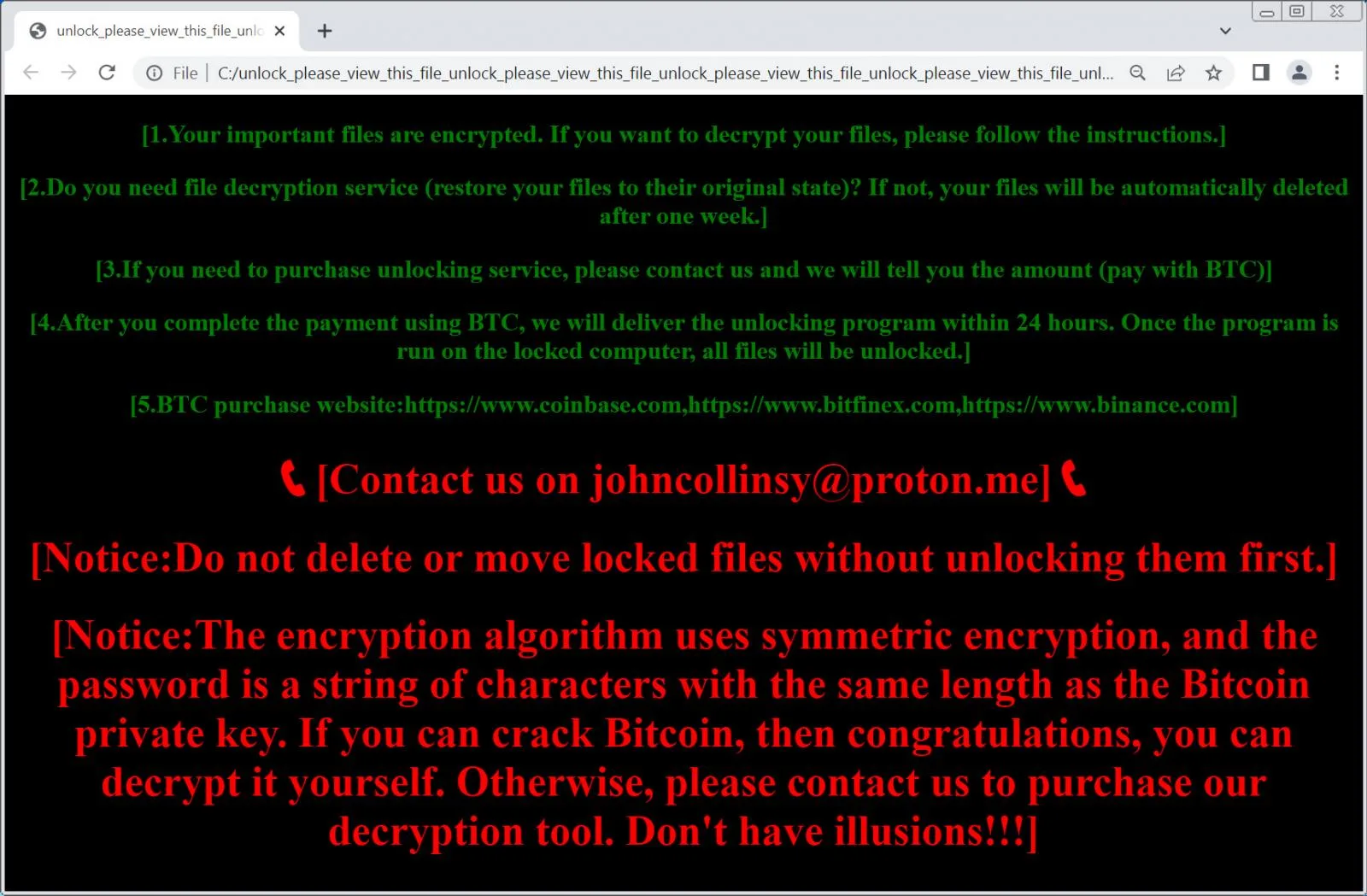
Source: Orange CERT
This ransom note instructs the victims to contact them at a disposable ProtonMail address, which, in a few cases seen by BleepingComputer, was johncollinsy@proton[.]me.
The ransom note does not indicate that data was stolen, which is odd for most modern ransomware operations.
Espionage and ransomware combined
Investigating deeper, Orange says they found some overlap between the content of the ransom note and a ransomware tool sold by a cybercrime group named Kodex Softwares (formerly Evil Extractor). However, there were no direct code overlaps, making the connection blurry.
Orange has shared several hypotheses for the attacks, including false flag operations meant to distract, strategic data theft operations doubled with revenue generation, and, more likely, a Chinese cyberespionage group "moonlighting" on the side to earn some money.
Only last week, Symantec reported about suspected Emperor Dragonfly (a.k.a. Bronze Starlight) operatives deploying RA World ransomware against Asian software firms and demanding a ransom of $2 million.
Compared to North Korean actors who are known to pursue multiple goals in parallel, including financial gains via ransomware attacks, Chinese state-backed actors haven't followed this approach, so the shift in tactics is concerning.
Related Articles:
Chinese espionage tools deployed in RA World ransomware attack
KuCoin to pay nearly $300 million in penalties after guilty plea
MirrorFace hackers targeting Japanese govt, politicians since 2019
White House links ninth telecom breach to Chinese hackers
CISA and FBI: Ghost ransomware breached orgs in 70 countries
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




