Ring is warning that a backend update bug is responsible for customers seeing a surge in unauthorized devices logged into their account on May 28th.
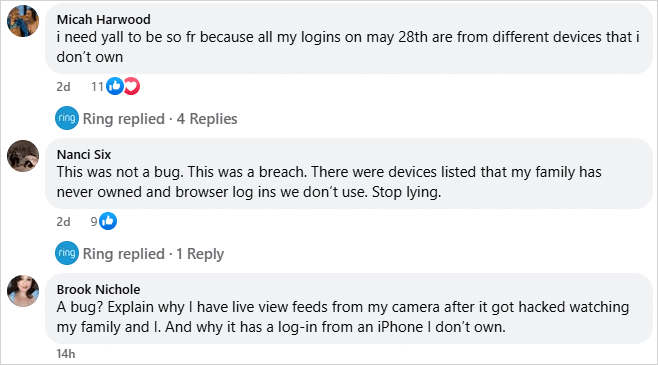
On May 28th, many Ring customers reported seeing unusual devices logged into their accounts from various locations worldwide, leading them to believe their accounts had been hacked.
Last week, Ring posted to Facebook stating that they are aware "of a bug that incorrectly displays prior login dates as May 28, 2025."
Ring also updated its status page to say that these unauthorized logins are caused by a bug in a backend update that was released.
"We are aware of an issue where information is displaying inaccurately in Control Center," reads Ring's status page.
"This is the result of a backend update, and we're working to resolve this. We have no reason to believe this is the result of unauthorized access to customer accounts."
These false login entries were all dated May 28, 2025, which lends some weight to Rings statement that this was a backend issue rather than a global hacking incident.
However, customers are not buying Ring's explanation, reporting that they saw unknown devices, strange IP addresses, and countries that they never visited listed in their Authorized Client Devices list, so they couldn't be previous logins.
"Absolute bollocks with your 'bug' I don't even know Derbhille or is she anyway associated with our ring camera or family? Just admit you've been hacked and yous are gonna amend this," a customer posted to X, while sharing a screenshot of login from a device named “derbhile’s iPhone.”
"I find it interesting that it's just a "bug" yet one of my several unknown logins from that date was a log in from Spain… I'm in Texas so doesn't seem like just a bug or log ins on prior devices because I can assure you I have never been to Spain," another customer posted to Facebook.
The sense that Amazon is hiding an actual security incident is further enhanced by the fact that a backend update should be easy to reverse. Yet, three days later, people are still seeing logins from devices they don't recognize.
To make matters worse, some users report seeing live view activity during times when no one in the household has accessed the app, and others report not receivingsecurity alerts or multi-factor authentication prompts when new devices are added.
Source: BleepingComputer
While this could be a bug displaying incorrect device names and logins, Ring should clearly state this, as it has instead stated that it was the user's previous logins.
BleepingComputer contacted Ring to inquire about the situation and why people are seeing devices and countries that they have never owned or been to, and thus cant be previous logins.
Ring users should review authorized devices from the app's Control Center > Authorized Client Devices section. If any devices or logins are not recognized, they should be removed immediately.
It would also be prudent to change your account password and enable two-factor authentication from the Account Settings.
[Update 7/22 2:15 AM EST] – An Amazon spokesperson sent BleepingComputer the following comment:
"We are aware of an issue where information is displaying inaccurately in Control Center. This is the result of a backend update, and we’re deploying a fix. We have no reason to believe this is the result of unauthorized access to customer accounts." – Amazon spokesperson
The spokesperson explained to BleepingComputer that the IPs and devices users see on the Authorized Client Devices page were used to login to the customer Ring account at some point in the past. These entries may include devices they no longer own, and devices for users who customers shared login information with.
The Board Report Deck CISOs Actually Use
CISOs know that getting board buy-in starts with a clear, strategic view of how cloud security drives business value.
This free, editable board report deck helps security leaders present risk, impact, and priorities in clear business terms. Turn security updates into meaningful conversations and faster decision-making in the boardroom.
Download the template to get started today
Related Articles:
HPE warns of hardcoded passwords in Aruba access points
Gigabyte motherboards vulnerable to UEFI malware bypassing Secure Boot
NVIDIA shares guidance to defend GDDR6 GPUs against Rowhammer attacks
Hikvision Canada ordered to cease operations over security risks
Get started in an Amazon dropshipping business with this course deal
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________





