SonicWall is warning that a recently fixed access control flaw tracked as CVE-2024-40766 in SonicOS is now "potentially" exploited in attacks, urging admins to apply patches as soon as possible.
"This vulnerability is potentially being exploited in the wild. Please apply the patch as soon as possible for affected products. The latest patch builds are available for download on mysonicwall.com,” warns the updated SonicWall advisory.
CVE-2024-40766 is a critical (CVSS v3 score: 9.3) access control flaw impacting SonicWall Firewall Gen 5 and Gen 6 devices, as well as Gen 7 devices.
The software vendor did not disclose much information about the flaw other than its potential for unauthorized resource access and ability to crash the firewall, thus eliminating network protections.
When SonicWall first disclosed the flaw on August 22, 2024, the flaw was only believed to be in the SonicWall SonicOS management access. With today’s update, the company is warning that CVE-2024-40766 also impacts the firewall’s SSLVPN feature.
Apply patches as soon as possible
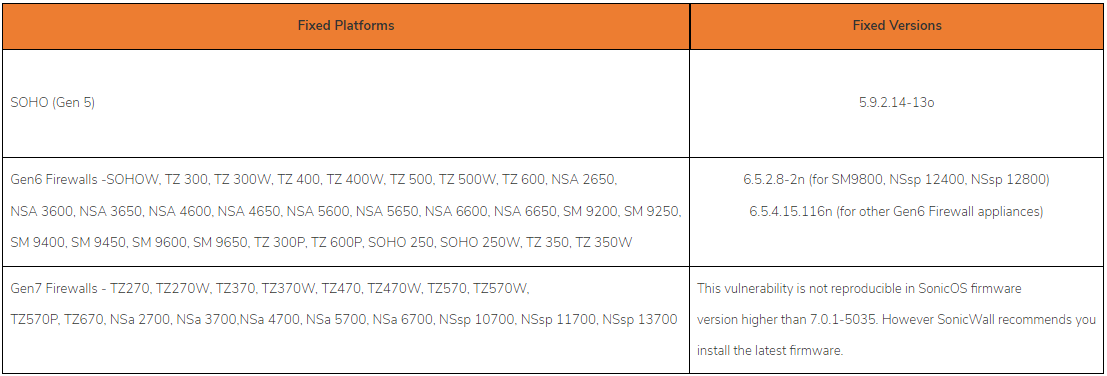
The list of impacted products and versions, as well as the releases that address CVE-2024-40766, are summarized as follows:
- SonicWall Gen 5 running SonicOS version 5.9.2.14-12o and older – fixed in SonicOS version 5.9.2.14-13o
- SonicWall Gen 6 running SonicOS version 6.5.4.14-109n and older – fixed in 6.5.2.8-2n (for SM9800, NSsp 12400, NSsp 12800) and version 6.5.4.15-116n (for other Gen 6 Firewalls)
- SonicWall Gen 7 running SonicOS version 7.0.1-5035 and older – not reproducible in 7.0.1-5035 and later.
The latest mitigation recommendations by SonicWall include:
- Limit firewall management to trusted sources and disable internet access to the WAN management portal if possible.
- Restrict SSLVPN access to trusted sources only and disable it entirely if not needed.
- For Gen 5 and Gen 6 devices, SSLVPN users with local accounts should update their passwords immediately and administrators should enable the "User must change password" option for local users.
- Enable multi-factor authentication (MFA) for all SSLVPN users using TOTP or email-based one-time passwords (OTPs). More information on how to configure this measure is available here.
While SonicWall has not shared how the flaw is being actively exploited, similar flaws have been used in the past to gain initial access to corporate networks.
Threat actors commonly target SonicWall as they are exposed to the internet to provide remote VPN access.
In March 2023, suspected Chinese hackers (UNC4540) targeted unpatched SonicWall Secure Mobile Access (SMA) devices to install custom malware that persisted through firmware upgrades.
BleepingComputer contacted SonicWall to learn more about how the flaw is being actively exploited in attacks, but a response was not immediately available.
Related Articles:
SonicWall warns of critical access control flaw in SonicOS
Google backports fix for Pixel EoP flaw to other Android devices
Microsoft August 2024 Patch Tuesday fixes 9 zero-days, 6 exploited
CISA warns about actively exploited Apache OFBiz RCE flaw
Critical ServiceNow RCE flaws actively exploited to steal credentials
Original Article Published at Bleeping Computer
________________________________________________________________________________________________________________________________




